
WordPress SEO by Yoast Hacked
The discovery of the WordPress SEO Vulnerability
Ryan Dewhurst, developer of a tool called WPScan and founder of Dewhurst Security, discovered this blind SQL injection vulnerability which was reported here by the Hacker News on March 11th, 2015. This quickly gained widespread attention in the WordPress community because the plugin has been downloaded more than 14 million times.
So, does this mean that 14 million people are immediately going to be affected by this vulnerability?
Absolutely not.
The chances that you are affected by the vulnerability are slim because the exploit requires the credentials of a logged in user being redirected to a malicious site which would then launch the blind SQL injection attack. As The Hacker News reports:
This can be achieved with the help of social engineering, where an attacker can trick an authorized user to click on a specially crafted payload exploitable URL.Mohit Kumar, The Hacker News
The WordPress SEO by Yoast: Quick Response
Joost de Valk, the developer of the plugin, responded and updated his plugin on the same day and issued this WordPress SEO Security Release.
In the response, Joost de Valk explains the how he heard about the vulnerability, why the WordPress SEO team missed it, and how you can update your WordPress SEO plugin to avoid being susceptible to an attack.
Most importantly, we learn of the cooperation between Ryan Dewhurst and Joost de Valk in making this matter public. Ryan, who stood to gain lots of attention and exposure from this “find”, notified Joost before going public with it. This allowed Joost time to come up with an upgrade to the plugin before the vulnerability was publicly exposed:
We were notified of this issue by Ryan Dewhurst of the WPScan team, who waited for us to release an update before publishing his find to the public, for which we thank him! This type of responsible disclosure is what keeps us all safe, but it only does so if you update.Joost de Valk
How to Upgrade Your WordPress SEO Plugin
The bottom line is this: Even though you will probably not fall victim to an attack, you must upgrade your WordPress SEO by Yoast plugin. And, fortunately for you, you were probably upgraded automatically.
Because this vulnerability could potentially affect literally millions of WordPress users, the team at WordPress.org forced this automatic update to most users. Thus, unless you turned WordPress automatic updates off, you have already been upgraded.
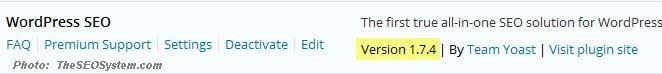
But, just to be sure, head over to your WordPress plugins tab and check your version of WordPress SEO. It should say version 1.7.4 or higher as you see in the photo below:
- The AI Inconsistency Gap: Why Your Brand is Winning on Google but Losing the “Answer War” - February 26, 2026
- The Personal Assistant Pivot: Optimizing for AI Search and AEO in 2026 - February 26, 2026
- The Ultimate Guide to Dental SEO: How to Rank Higher & Attract More Patients - March 10, 2025

